Previously, if one wanted hardware accelerated transcoding in one’s Plex Media Server, the options were to either use a Nvidia card, or use an Intel CPU with QuickSync (and a platform that enables the iGPU). With Intel releasing the Arc series of GPUs, a 3rd option emerged. Recently, low profile variants of both the Arc A380 and Arc A310 have become widely available, presenting a low cost, low power, and easy to fit hardware transcoding option. On the software side, not much is needed to get hardware accelerated transcoding working with the Arc A380/A310.
Drivers
First up, you will need the Intel graphics drivers in your kernel. Check your distro’s guides for how to do this (Gentoo has a fairly good wiki entry on this). One item to note, the choice of whether to compile the driver as a module or include it in the kernel depends on your setup. A general rule of thumb that has worked for me: if you use an initramfs, compile the DRM_I915 driver as a module; if you use efistub as your bootloader, build the driver into your kernel and include the firmware into the kernel image.
If you need to include the firmware into the kernel image (building the DRM_I915 driver into the kernel instead of as a module), you will need to install the linux-firmware package before compiling your kernel. Under the firmware loader settings, you’ll need to include the following firmware blobs: the dg2_dmc, dg2_guc, and dg2_huc. As of Linux 6.4.13 these are the versions the i915 driver will want: i915/dg2_dmc_ver2_08.bin i915/dg2_guc_70.bin i915/dg2_huc_gsc.bin
Userland
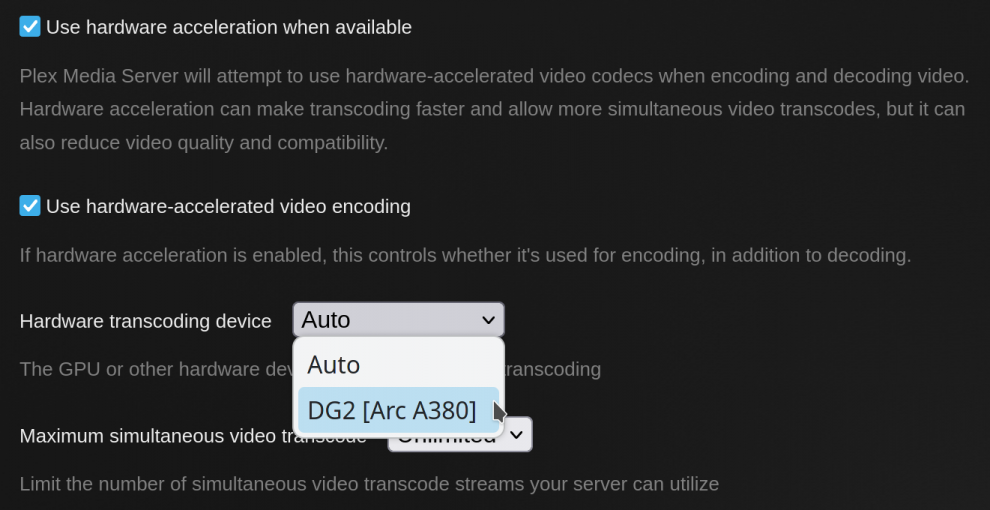
After rebooting with the new kernel, within the Plex Settings, under the Transcoding section, enabling hardware acceleration should be available. Additionally, the Arc A380/A310 should show up in the Hardware transcoding device dropdown. Make sure both “Use hardware acceleration when available” and “Use hardware-accelerated video encoding” are checked. For the “Hardware transcoding device” option, if you have other GPUs, you may want to select the Arc device so it is targeted. Don’t forget to press the “Save Changes” button.
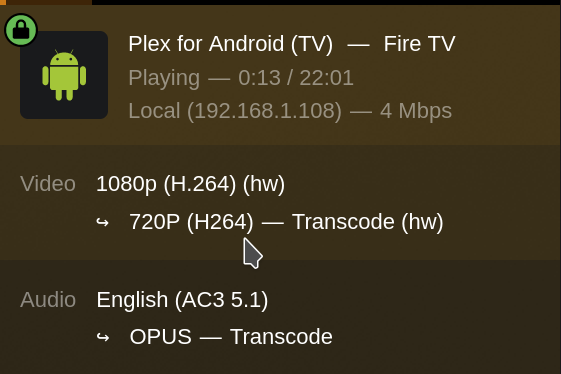
While Plex is now finding the device, it still may not be able to use it just yet. If libva isn’t installed, Plex will not be able to use the Arc GPU for transcoding. For funtoo users, ensure that your profile has the gfxcard-intel mix-in and then install libva. At this point, hardware transcoding should work. You can double check this by using intel_gpu_top while playing a video. Another method of checking if hardware transcoding is working is through the “Now Playing” section of the Plex dashboard. If you see a (hw) next to the codec and the word Transcode in the video section, hardware transcoding is working.
Note that getting hardware transcoding working with Plex Media Server only required the Intel graphics Linux kernel driver, some firmware blobs, and libva. X server, Wayland, a window manager, and desktop environment were not needed or installed.
-John Havlik
