This morning, at about 12:18AM CDT, someone sent out a mass phishing email to many University of Minnesota students. They claimed to be TCF Bank and there was some sort of a security issue which required account re-validation (even at 3:00AM, when I read, it I knew something smelt phishy).
The e-mail
Dear TCF Bank Customer,
We have detected 3rd-party intrusions in many of our customers account, and because your security is our primary concern, we have limited your account until you confirm your identity and verify that your account has not been used for fraud purposes.
To access our online account validation form and remove the limitations on your account, please click on the following link:
Click here to access the validation form
After you complete our online validation form your account limitations will be removed and you can begin using your account as usual.
Thank you for taking your time,
TCF Bank Security Office.
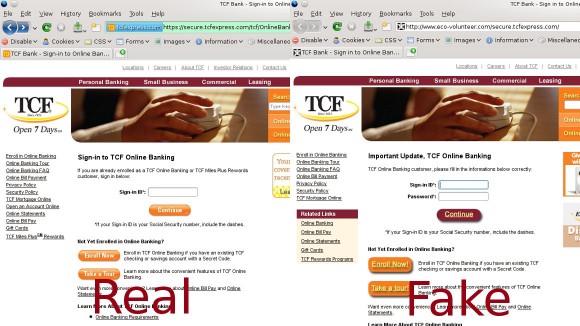
Unlike a normal, reply with details phishing attempt, this one had a link for a validation form. Naturally, this goes to a fake page, under a totally different URL than anything on TCF’s website (it is http://www.eco-volunteer.com/secure.tcfexpress.com/ for those who care). And, you guessed it, the page is not served over SSL as it should be. However, the form is scraped from TCF’s site, and hotlinks images from TCF’s servers (big no-no as that is illegal—as if phishing wasn’t already illegal). However, it does look like the TCF page, except for a few differences.
The Scam Site
First, TCF never asks for your password and login id at the same time. This has been the case for as long as I can remember. The second issue with the page, is minor and I doubt people will be able to tell. TCF has done a little bit of design tweaking, which makes the buttons look different on the real site, along with a few items changing. The causal user would probably never notice.
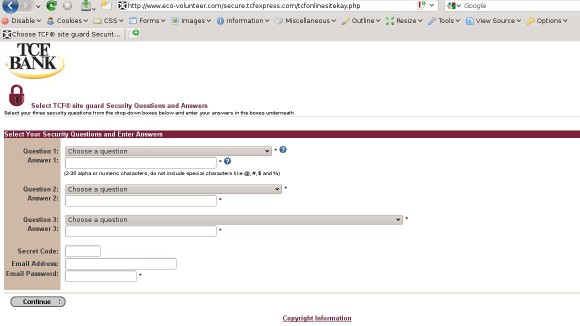
After providing (hopefully bogus) information, the user will be greeted with a second page. This one mimics the secondary page that TCF uses when logging on, but asks for the wrong information. The page asks for your three secret questions and answers, your secret code (ATM PIN), your e-mail address, and the password for your e-mail address. This should scream that it is a phishing site, no one other than yourself needs to know your e-mail password.
According to TCF’s website, this phishing attempt was sent out to many University of Minnesota and Saint Cloud State University students this morning. Unfortunately, instead of detailing the phishing attack, they provide a generic description of a phishing scam.
Biting Back
Want to make a difference? There are a few things you can do.
- If you have received these emails, forward them to abuse@umn.edu (for those associated with the University of Minnesota, for St. Cloud State you could try abuse@stcloudstate.edu) and emailfraud@tcfbank.com.
- Report the site to Google as a phishing site by going to the Google Report a Phishing Site page. Once it is recognized as a threat, all Firefox and Chrome users will receive the “Get me out of here” screen rather than the page. The URL to the phishing site is: http://www.eco-volunteer.com/secure.tcfexpress.com/
- Go to the phishing site and provide bogus information (needs to “look real” but must not be real). A deluge of real looking, yet bogus information will waste the scammer’s time, resources, and potentially reduce the damage of the attack. Oh, and it may anger the scammer, which is a good thing.
-John Havlik
[end of transmission, stay tuned]

Actually I disagree with the suggestion of providing false information. You run the risk of providing someone else’s real information. Also the scammers may take the information that you submit and try it against the bank’s website. That’s just an attack on them that you’ve caused.
Kind of like that wordpress anti comment spam plugin from a few years back that forwarded comment spammers onto the FBI website. That went over well.
If done correctly, and providing weak passwords and pass-phrases to the phishers, I’m sure statistics are on out side (i.e. there little chance of providing a real username and correct password for it). If there was an actual collision (provided a real username and the correct password for it), it is the fault of the bank for allowing weak passwords and the user for having too weak of a password.
-John Havlik